Learn how Netpluz Managed SOC helps you detect breaches early and respond quickly
You can’t protect or detect what you can’t see, and hackers are very good at covering their tracks. That’s why you need 360° Degree Visibility, which covers your entire attack surface and pieces together complex attacks from a host of weak signals that would otherwise be missed.
Defend against the constantly evolving cyber threats with 24/7 detection and response on the entire attack surface. Netpluz Asia’s in-house Security Operations Centre (SOC), powered by Stellar Cyber, the industry’s first Open Extended Detection & Response (OPEN-XDR) platform, are engineered for maximum cyber monitoring, protection and response.
Watch the on-demand webinar whenever and wherever you want.
SecOps Is the Path Forward
An increasingly complex attack surface, as well as greater usage of the cloud and hybrid IT, were already threatening the cyber-resiliency of many enterprises prior to the pandemic. However, solving the challenges is not impossible.
This on-demand webinar is for anyone that is interested in overcoming the SecOps challenges by ensuring resiliency and secure protection towards the enterprises with a single platform and improving detection and response with a lean SecOps team at the price an organization can afford.
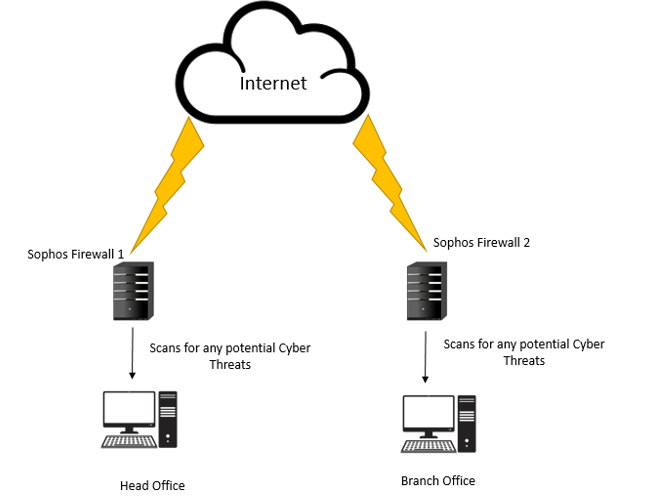
Simplifying Cloud Connectivity with Secure SD-WAN
Explore Secure SD-WAN with Netpluz Asia to deliver fast, scalable, and flexible security-driven networking for cloud-first, security-sensitive, and fast growing business
Small and medium-sized enterprises (SMEs) that operate from multiple locations or branches often find themselves relying on low bandwidth internet connections to access their corporate applications or data.
Software-defined wide-area networking (SD-WAN) is rapidly replacing traditional WAN for remote office and branch deployments. While SD-WAN offers performance benefits that support new digital innovations, many SD-WAN solutions lack consolidated networking and security features. In response, many network leaders have had to add a complex assortment of tools and solutions to manage and protect their SD-WAN deployments. Instead, they need a simplified approach to contain costs, improve efficiency, and reduce risks.
Watch Rueburn Liang of Netpluz Asia, and Chin Ping of Fortinet to discover the reason how SD-WAN automates network traffic over private, wireless, and broadband connections, and provide SMEs with a cost-effective and secure cloud-based WAN connection.
.png?width=600&height=600&name=Untitled%20design%20(5).png)
Fortinet Secure SD-WAN the #1 in 2021 Gartner® Critical Capabilities for WAN Edge Infrastructure
In the 2021 Gartner® Critical Capabilities for WAN Edge Infrastructure, Fortinet ranked #1 in the Remote Worker Use Case, a new addition to the report this year.
The Traditional WAN Challenges
If you are facing these challenges, then this webinar is definitely for you!
-
Security Concern
Deploying any new WAN technology can introduce unintended
-
Unpredictable Performance
Prioritizing data over VPN between branches is difficult and causes performance challenges of key applications
-
High Cost
Traditional WAN, especially MPLS, requires a single provider to access many sites that involve higher costs.
-
Troubleshooting Issue
If there are issues in the network, it is difficult to pinpoint the exact cause due to their broad coverage of geographical areas.
eSentinel™ approved by MAS Singapore for Digital Acceleration Grant (DAG)
Netpluz Asia is thrilled to be named an approved vendor by MAS for eSentinel™, our born-in-the-cloud 360° cybersecurity solution, as part of the general solutions – security-related solutions. Organisations can now get up to 80% co-funding for the implementation of eSentinel™ to strengthen your IT Infrastructure & Data security.
In 2019, the global economy has experienced the disruptive effects of the global Coronavirus pandemic and Singapore was no exception. It was one of the hardest hits in Asia. Companies were forced to active business continuity plans, such as remote work for the first time and many were not prepared for it. The financial sector, like so many others greatly affected, was forced to adapt quickly in order to remain operational throughout this time.
To assist companies in the financial sector, the Monetary Authority of Singapore (MAS) introduced a SGD 125 million support package. Out of SGD 125 million support package, SGD 35 million were designated for strengthening and accelerating the digitalisation and operational efforts of these industries through the Digital Acceleration Grant (DAG).
DAG scheme aims to help Singapore-based smaller financial institutions with less than 200 employees, to adopt digital solutions to improve productivity, increase efficiency, enhance operational resilience, manage risks, and serve customers better.
Working with Netpluz Asia, you can get up to 80% co-funding to implement eSentinel™ to strengthen your IT Infrastructure & Data security, Cybersecurity Operations as well as Periodic Cybersecurity Assessments, under a true single pane of glass reporting.
Scheme Parameters

How to Apply
General Solutions
If the solution intended for claim can be found in the General Solutions List, (404.2 KB)your solution is qualified for DAG co-funding. Please fill and submit this General Solutions application form (255.8 KB) to fintech_office@mas.gov.sg at the end of your funding period.
All solutions must be used for at least 6 months before the submission of your application form. Funding will be done on a reimbursement basis.
Other awards & accolades:

About Netpluz
NETPLUZ is formed by a team of highly competent infocomm professionals with more than 15 years of deep industry expertise and proven experience. Firmly believing that communications form the backbone of any business, NETPLUZ simplifies and satisfies communication needs of our clients through the delivery of high quality Managed Data, Voice, Video and Cyber Security services over a single, converged network. Backed by a strong technical support team, NETPLUZ managed services are designed and operationalized with cost efficiency and business productivity as the baseline, with uncompromising service standards. For more information on Netpluz Managed Services, contact us at contact@netpluz.asia or visit us online at www.netpluz.asia.
Media Contact:
Rueburn Liang
Senior Marketing Manager
Netpluz Asia Pte Ltd
Phone: +65 6805 8917
Email: rueburn.liang@netpluz.asia
Protect Against Advanced Email-Based Attacks
Wednesday, 24 February 2021, 2PM – 3PM
Email phishing is one of the greatest security threats facing organisations globally. With the pandemic accelerating digital transformation and with workforce disconnected from the secured private network of offices to work from anywhere, you need a way to protect your workforce from such attacks. A click from an unsuspecting employee, may well place your entire network compromised.
Countless individuals and organisations have unwittingly transferred money, sent confidential documents, and emailed credentials to cyber criminals who were impersonating their boss, colleague, or a trusted customer. These targeted attacks can be very compelling and cannot be stopped with existing email security solutions such as Anti-Spam & Anti-Virus (ASAV) solution — creating devastating results for individuals, businesses, and brands.
Learn more about the current threat landscape observed by a SOC team, business challenges, as well as the defense you need to have in place to defend against them.
Key takeaways:
- Cyber security predictions for email protection
- Landscape – Top 3 email threats observed
- Security challenges of the new mobile workforce
- Who is at highest risk within your organisation
- Identifying phishing email
- The difference between phishing and spear phishing, and why it matters
- The techniques used in impersonation and spoofing attacks, and how to spot them
- How eSentinel – Email Protection stacks up against ASAV, the differences and why it matters
- How to manage repeat clickers of malicious emails
Data Breach – When Traditional Layers Of Cybersecurity Fail
“How Prepared Are You?”
What happens when your traditional layers of cybersecurity fail? How can you stay ahead of the game? Nobody could ever be prepared enough when it comes to cybersecurity. The best that one can do is to expect the worst and be ready to receive the impact when it comes.
The Age of Digitalisation brought much success to many businesses, be it SMEs or big corporations. However, with these success stories, an alarming number of cyber attacks are reported in recent years. These cyber attacks hinder businesses and greatly affect many aspects such as credibility, work efficiency and most importantly loss in revenue. Cyber attacks can come in various forms, examples include malware, phishing emails and more which can lead to possible data breaches.
According to a 2019 survey by endpoint security firm, Carbon Black, 96% of the surveyed Singapore firms have had data breaches due to cyber attacks. The results are worrying as data breaches can impact a business financially to a huge extent. These attacks are estimated to cost Singaporean businesses $1.7million per breach, according to Channel Asia. These numbers can easily cripple and crumble many SMEs that are not financially ready to receive such an impact. In Singapore and Malaysia, SMEs contribute to 40% each for their nation’s GDP, translating that the importance of SMEs in these countries.
With the recent changes to the Personal Data Protection Act (PDPA) in Singapore, businesses that are found guilty of a data breach are now expected to pay a heftier fine based on their annual company turnover. This is to ensure a safer environment in the digitised world by strengthening data protection standards. From SMEs to big corporations, there is always much valuable and personal data that can be potentially compromised. The data may include customer’s personal data as well as employee’s personal data such as NRIC, Date of Birth, residential addresses and bank information. In recent news, Eatigo reported a data breach with potentially 2.8 million accounts illegally accessed. Similarly, Lazada, reported a data breach from their recent acquisition, RedMart. It was reported that personal information from 1.1million RedMart accounts was stolen as a result of the data breach.
If you think that SMEs are safe from cyber attacks, you are wrong. In fact, 43% of cyber attacks were reportedly targeted at SMEs. In 2019, Homegrown fashion label, Love, Bonito reported a data breach with their users’ information compromised. SMEs may not be able to cushion such an impact financially compared to big corporations with deep pockets, especially with the new amendment to the PDPA. For many SMEs, it could mean the closure of businesses. However, there are certain measures that SMEs could implement to prevent being caught in such a situation.
Hire an external consultant
Businesses should always be looking towards increasing productivity and efficiency that translates to revenue. This is why hiring an external consultant or a service provider to manage your data and cybersecurity needs is vital. Businesses shouldn’t be worrying about scouting for cybersecurity talents. Not only are they much more costly, it is also more feasible to let a team of experts who specialise in specific areas of expertise, manage your data and security solutions. In addition, they are well equipped with knowledge and experience which can definitely bring much value in the event of a cyber attack. Hence, there is a business case for engaging MSPs to handle cybersecurity as it is more cost efficient.
Let the experts manage and mitigate cyber risks while your business focus on the main goal of profiting.
Employee Training

You can be well protected in every aspect, thinking there are no loopholes. However, research has shown that more often than not employees unknowingly aid in cyber attacks leading to data breaches. According to Security Magazine, employees are behind 4 in 10 data breaches. Phishing emails and file-based malware are among a few common deceits that employees usually fall for. This suggests a strong need for businesses to provide frequent training on cybersecurity for their employees as they are the weakest link.
The Failsafe
The big question: WHAT IF? When all else fails, what can businesses rely on? Most businesses may already have security measures implemented to prevent cyber attacks however, in the worst case scenario, a data breach might still happen.

Cyber insurance helps businesses cushion their financial impact in the case of a cyber attack and data breach. For example, during an email phishing incident, cyber insurance covers the entire cost of the forensics process which is a huge financial setback for businesses if not insured. In ransomware incidents, bitcoins are usually the currency requested to be paid in. However, if insured, the ransom fee would be covered in full. SMEs can easily crumble if caught in situations like these, paying a huge sum of money for forensics and bitcoins.
Where and How to Get Covered?
Netpluz Asia is the first Managed Communications Service Provider (MSP) to introduce cyber insurance into our existing wide array of comprehensive data, voice and video solutions. As a one-stop MSP with 24/7 support, Netpluz Asia can help spur your businesses on to greater heights while making the journey smooth and secure by the delivery of high quality services.
An upcoming webinar by Netpluz Asia featuring Commercial Director, Kenneth Wee and guest speaker from Chubb, Elsa Xu, Financial Lines Manager, aims to highlight the topic of cybersecurity management, risk transfer and how insurance comes into play.
To find out more about the webinar and cyber insurance click here
References:
Baharudin, Hariz. “Love, Bonito Customers’ Data Breached, Credit Card Details Exposed, Watchdog Investigating.” The Straits Times, 13 Dec. 2019, www.straitstimes.com/tech/love-bonito-customers-data-breached-credit-card-details-exposed-watchdog-investigating.
“Carbon Black Reveals 96 Percent of Firms in Singapore Suffer Data Breaches.” CISO MAG | Cyber Security Magazine, 3 Oct. 2019, cisomag.eccouncil.org/around-96-percent-of-singapore-businesses-suffer-data-breach-survey/#:~:text=Around%2096%20percent%20of%20Singapore%20Businesses%20Suffer%20Data%20Breach%3A%20Survey,-By&text=According%20to%20the%20research%20findings,an%20increase%20in%20attack%20volumes.
“Eatigo Reports Data Breach, Personal Data from Customer Accounts Listed for Sale Online.” CNA, www.channelnewsasia.com/news/singapore/eatigo-data-breach-personal-information-millions-account-13425082.
Henderson, James. “Security Attacks Cost Singaporean Businesses $1.7M per Breach.” Channel Asia, www.channelasia.tech/article/670400/security-attacks-cost-singaporean-businesses-1-7m-per-breach/.
Kapur, Ricky. “Cybersecurity for Small-and-Medium Enterprises in Asia Pacific.” Microsoft Stories Asia, 29 Oct. 2020, news.microsoft.com/apac/2020/10/29/cybersecurity-for-small-and-medium-enterprises-in-asia-pacific/.
“Lazada Suffers Data Breach; Personal Information from 1.1 Million RedMart Accounts for Sale Online.” TODAYonline, www.todayonline.com/singapore/lazada-suffers-data-breach-personal-information-11-million-redmart-accounts-sale-online.
“Microsoft: Digital Transformation Doesn’t Make SMEs Immune to Cyber Threats.” Securitybrief.Asia, securitybrief.asia/story/microsoft-digital-transformation-doesn-t-make-smes-immune-to-cyber-threats.
“Stressed Employees behind 4 in 10 Data Breaches.” Www.Securitymagazine.com, www.securitymagazine.com/articles/93921-stressed-employees-behind-4-in-10-data-breaches.
Wong, Lester. “Parliament: Proposed Changes to PDPA Include Stiffer Fines for Data Breaches, Mandatory Notification When They Occur.” The Straits Times, 5 Oct. 2020, www.straitstimes.com/politics/parliament-proposed-changes-in-law-include-stiffer-fines-for-data-breaches-mandatory.
Author: Sebastian Toh
Webinar | Cyber Risk Management in the New Digitalisation Age
Cybersecurity Management and Risks Transfer
Considering the complex, dynamic network and devices that businesses must govern across firewalls, applications and cloud – Cybersecurity is no longer optional. Amendments made recently to the recent Personal Data Protection Act (PDPA) Bill will continue to have meaningful impact on businesses throughout 2021. Over the past year, there were numerous breaches and cyber-attacks and it is expected to continue with cyber threat landscape evolving at a fast pace.
Simple and hard truth is that cybersecurity is good for business. Compliance to cybersecurity help you maintain your customers and brand loyalty — setting your business ahead and apart from the rest of the competition.
Ultimately, addressing specific cybersecurity risks that affect your business’s network and data security can be daunting, complex and costly to manage, which leads to many businesses overlooking its importance.
In this webinar, we will be sharing the latest cybersecurity challenges, introducing solutions and strategies that are both practical and cost-effective in protecting your business from the cybersecurity and data breaches. Register now to learn more about how to take on cybersecurity risk, compliance and management, putting your business ahead of the curve.
Takeaways include:
- Cyber risks landscape today
- Identify your weakest links
- Business implications in the event of cyber-attack and data breach
- Mitigate & Transfer your cyber risks
- And many more…
Join Kenneth Wee, Commercial Director at Netpluz and Elsa Xu, Financial Lines Manager at Chubb Insurance as they walk you through how to build up your business cyber resilience and mitigate risk that often businesses overlook, especially in this digitalisation age and the evolving modern workforce.
Watch the webinar recording below to find out more information!
Webinar Recording
Presentation Slides
Webinar | Understanding the Life Cycle of a DDoS Attack
Webinar is over. To find out more, please contact us at contact@netpluz.asia.
With the new normal as a result of the recent COVID-19 pandemic, there is a surge on the use of online services. Availability and security of these services should be the topmost priority to ensure business continuity and achieve its targets. In the past six months, Nexusguard and Netpluz witnessed the rise in online threats and DDoS attacks. Given this, these two Companies can provide services to mitigate the threats and reduce the risk of service outages.
In this webinar, we will discuss the DDoS life cycle which will help us understand the basic function of a Security Operations Center specializing in DDoS mitigation.
Join this webinar to discover:
- DDoS Threat Intelligence Review Q2 2020
- DDoS Attack Life Cycle
- Overview of DDoS Scrubbing Centres
- In Country + Global Mitigation Setup
- Hands-on learnings to build your in-demand cybersecurity practitioner profile
- And more..
The presenters
Mandy I. Tupaz
Senior Manager for Services and Security Operations
Mandy Tupaz, Senior Manager for Services and Security Operations for Nexusguard, has been in the industry of Network and Security Operations for almost 15 years. He was able to witness the evolution of DDoS Attacks from small and simple to complex and large DDoS Attacks. A proven frontliner who is versed in supporting the global market ensuring Online Threats are mitigated and online services will be made available.
Ruben Martin Mondejar Jr
Business Development Director
Ruben is a seasoned cyber security specialist with a cumulative experience of 16 Years in the Information Security industry, majority of which he has spent focusing on malware analysis, SOC/CSIRT design, threat intelligence and incident response. He has conducted training for various national CERTs and Law Enforcement across APJ. He collaborated with researchers like the Center for Security Studies in Zurich on cyber security policy making. He is a cybersecurity advocate and educator. During his personal time he does pro bono workshops, he serves as advisory council member to Philippine law enforcement and consultant to government, politicians and armed forces whenever the need arises. The highlight of his career is that he commanded 2 command center(s) in Singapore during the Anonymous attack in 2013 against the Singapore Government.
Webinar Recording | Fight Against the Rise of Ransomware
Click the video to play – Source:Youtube.com
Stories of organizations crippled by ransomware regularly dominate the IT news headlines, and accounts of six- and seven-figure ransom demands are commonplace. But, do the news stories tell the full story?
Based on an independent survey of 5,000 IT managers across 26 countries, the findings provide brand new insight into what actually happens once ransomware hits. Be prepared to be surprised.
Watch the webinar recording to discover:
• How many organisations were hit by ransomware last year, and which countries suffered most
• Which industries are hit hardest by ransomware (hint: it’s not the public sector)
• How many organizations pay the ransom to get their data back, and how many use backups
• The Cyber Security and Data Protection strategy
Presentation slides to view
LIVE Webinar | Understanding SME’s Obligation in Data Protection and Cybersecurity
Zooming into the responsibilities of Business, IT and Compliance during and post COVID-19
26 June 2020 | 2.30 PM to 4.00 PM
We know the importance of PDPA and we wanted to share that knowledge with our clients so take this opportunity to uncover what PDPA means for your company and department through this complimentary webinar with Straits Interactive, one of the experts in the field of data protection.
SMEs today operate in an increasingly connected and competitive digital economy where individuals’ online and real-world activities generate huge amounts of data, especially during circuit-breaker where everyone must work remotely from home.
SMEs have had to scramble to arrange employees to connect back to the office. Have you taken a look at the privacy and IT risks involved in using the free apps as well as the paid apps? Do you know what you need to look out for? No matter how good your multiple cybersecurity tools are, an attacker will eventually find a way into your network through vulnerabilities during a lapse. Join us for the 1-hour session with Straits Interactive to find out about the role and accountability of IT departments, and approach to mitigate the cyber threat and risk.
Topics covered:
- Latest PDPA updates
- Digitalisation & WFH Risks
- Roadmap to PDPA Compliance
- The common problems faced by businesses
- eSentinel™ – 360° Defense in Depth
- and many more!
The Presenters:
- Alvin Toh, Chief Marketing Officer, Straits Interactive Pte Ltd
- Kenneth Wee, Commercial Director, Netpluz Asia Pte Ltd
Webinar: eSentinel™ – 360° Managed Cybersecurity, Simplified
No matter how good your multiple cybersecurity tools are, an attacker will eventually find a way into your network through vulnerabilities.
Once cybercriminals acquire unauthorised access, you can only depend on the speed and performance of your IT team, to identify the threats, to manage multiple platforms to mitigate the attack. However, the time to respond and mitigate could last for hours or even days.
Join us for the 1-hour session to find out how you can now extend your cyber defense perimeter at the ISP level
We will be covering topics such as:
- The Cybersecurity landscape
- The common problems faced by businesses
- What is eSentinel™?
- 360° Defense in Depth
- and many more!
Webinar recording and presentation slides coming soon!
Cyber Security is the protection of not only internet-connected systems (including hardware, software or electronic data) from theft or damage by cybercriminals but also from disruption of services following a successful cyber-attack.[1] According to the Cyber Security Agency of Singapore, 378 business email impersonation scams were recorded in 2018. This led to businesses in Singapore suffering close to S$58 million in losses. [2] Cybersecurity Ventures has reported that businesses will lose approximately $6 trillion to cyber-crime by 2021. [3]
One of the key challenges faced by organisations today is implementing cybersecurity measures to protect their internet-connected systems from the continuously evolving nature of cyber-attacks. And according to Code 42, 78% of security professionals believe that the biggest threat to cybersecurity is the negligence of employees. [4]
Cybercriminals exploit the weakest links in an organization’s IT security fabric. Often, the weakest link in any organisation is the employees. And yet a study of over 5,000 businesses around the globe by Kaspersky Lab and B2B International found that just over half of businesses (52%) believed that their cybersecurity would be at risk because of their employees. [5]

Common Cybersecurity Mistakes Made By Employees
In this section, we’ll be looking at the four principal errors made by employees that could expose organisations to cyber-attacks
1. Weak and Vulnerable Passwords
According to security experts, poor password management contributes to 81% of the data breaches.[6] With employees utilising the same password for multiple accounts, not changing passwords on a regular basis and using weak passwords (some examples as shown in the table below) put organisations at risk. [7]
Examples of weak passwords:
|
Password |
Type |
|
kathy5 |
Name-based |
|
Qwerty |
Keyboard sequence |
|
AbcAbc |
Repeating sequence |
|
dr1v3way |
Word-based with common letter and number substitution |
- Weak or Outdated Security Software
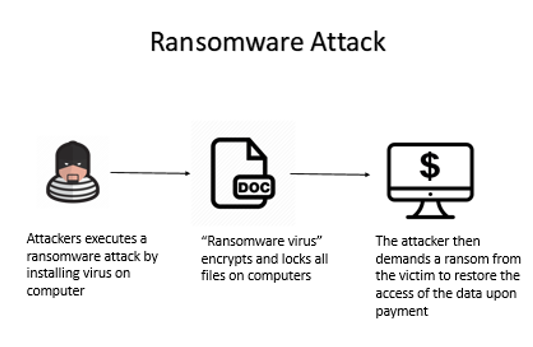
Keeping security software, web browsers and operating systems updated with the latest protection will deter cybercriminals from leveraging system vulnerabilities. However, many organizations do not keep up with the updates or fail to understand the consequences of not doing so. The consequences of an employee’s negligence could lead to a ransomware outbreak where the virus encrypts and locks all the files on the computer. The attacker then demands a ransom from the victim to restore the access of the data upon payment. [7]
Here is a diagram to illustrate how a Ransomware Attack is executed:
- Lax Email Practices
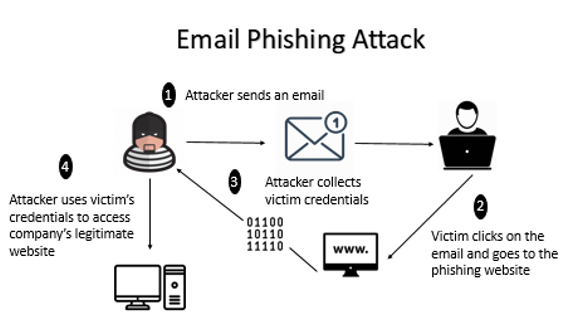
Despite repeated warnings against responding to unsolicited emails or text messages, employees continue to be targets of cyber-attacks such as phishing, social engineering, and smishing. These attacks occur when an attacker sends an email link to the victim. Upon clicking on the link, the victim will be directed to the phishing website where the attacker is able to collect the credentials of the victim. The attacker then uses the victim’s credentials to access the legitimate company’s website. [7]
Here is a diagram to illustrate how Email Phishing Attack is executed:
- Using Unsecured Networks
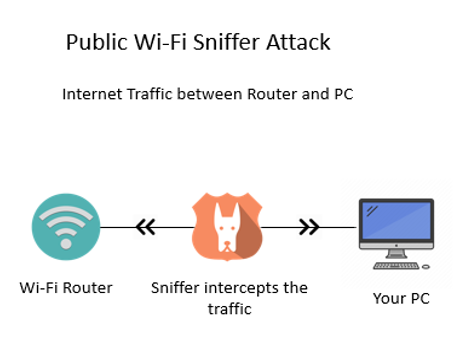
Utilising company devices on unknown networks increases the risk of cyber-attacks since data may not be encrypted over these networks and could easily be intercepted and subsequently stolen. For example, login details information can be revealed when there is an attempt to access emails on a public network. [7]
Here is a diagram to illustrate how a Public Wi-Fi Sniffer Attack is executed:
How can your company reduce these vulnerabilities?
In recent years, cyber-attacks have become more sophisticated and persistent due to weak security regulations enforced by companies. By now, you might be wondering how you could protect your data better. Sophos Intercept X Advanced with EDR and Druva inSync offer some possibilities that could help companies overcome poor practices done by their employees. These two products address the business challenges faced by organisations such as data protection, secure file sync and sharing, etc.
What is Sophos Intercept X Advanced with EDR?
Sophos Intercept X Advanced with Endpoint Detection and Response (EDR) is designed to stop the widest range of attacks. It can detect malware, provide exploit protection, defend against ransomware and more through a combination of modern and leading-edge foundation techniques. In an event of malicious activity, EDR provides users with a complete solution by providing them with a detailed report of the attack. This helps businesses understand the root cause of the attack and help them to avoid future cyber-attacks. [8]
Benefits of Implementing Sophos Intercept X Advanced with EDR

1) Deep Learning Malware Detection
Intercept X’s artificial intelligence is a deep learning neural network, an advanced form of machine learning that detects known and unknown malware without relying on signatures. Powered by deep learning detection, Intercept X has the best malware detection platform in the industry. This allows Intercept X to detect malware that slips by other endpoint security tools. [8]

2) Secured Data & Files
Intercept X utilises CryptoGuard technology to combat cyber security attack such as ransomware and boot-record attacks, making it the most sophisticated anti-ransomware technology available. Even if trustworthy files or processes are manipulated or stolen, CryptoGuard is able to interrupt and revert them to their original state. [8]
3) Detailed Report Analysis
With EDR, most threats are stopped before they can cause damage. Intercept X Advanced with EDR provides additional cybersecurity assurance with the ability to detect, investigate and respond to potential security threats. Thus, when a potentially suspicious file is detected the administrators are provided with an analysis of what the malware did and how it was executed. This helps your companies to understand the threats better and prevent them. [8]
Here is a quick overview of how Sophos Intercept X Advanced with EDR works:
What is Druva inSync?
Druva inSync provides a comprehensive solution for enterprise-grade data protection and management. It allows users to view their data sources and usage activities to ensure compliance. Administrators are also updated of any potential data risks that have been detected. Data collected are stored in a central repository, giving end-users seamless and constant access to the information. [9]
Benefits of Implementing Druva inSync
1) Centralised Data
Druva inSync allows collection of data through multiple devices like mobile phones and cloud-based applications. The collected data will be then stored and indexed in a central repository which makes it easier for an IT department to implement company policies. [9]

2) Real-Time Data Monitoring
Druva inSync is equipped with an administrative dashboard where users can monitor their data activities and data usage in real-time. This allows administrators to easily discover compliance issues and resolve them quickly before they grow into larger problems. Real-time data monitoring also keeps your organisations safe. [9]
3) Ease of Compliance Enforcement
Druva inSync helps you save time when it comes to administering policies and regulations. This system comes with pre-configured compliance templates like PCI, GLBA and HIPPA. It also enables users to customise and create their own templates. Whichever template one chooses, one can be ensured that the app automatically search for any data risks. [9]

What other solutions can you integrate along with Sophos?
Cyber-attacks are carried out mostly through emails and unsecured networks. This could be resolved by integrating the following products with Sophos Intercept X Advanced with EDR. [10]
|
Solutions: |
Features: |
|
Intercept X and Sophos Email |
✔ Validates if malware has been installed on devices with compromised mailboxes |
|
Intercept X and Sophos Wireless |
✔ Blocks worm-like lateral movement, automatically isolating infected machines ✔ Prevents non-compliant devices from connecting to corporate data |
Summary- Sophos Intercept X Advanced with EDR and Durva Insync
There are many comprehensive cyber security products available in the market to mitigate cyber-attacks. Needless to say, the product chosen to safeguard the data plays a major role in preventing cyber-attacks against your companies.
Here is a quick summary of the benefits of Sophos Intercept X Advanced with EDR and Durva InSync:
|
|
Sophos Intercept X Advanced with EDR |
Durva inSync
|
|
Deep Learning Malware Detection |
✔ |
|
|
Secured Data Files |
✔ |
|
|
Detailed Report Analysis |
✔ |
✔ |
|
Centralised Data |
|
✔ |
|
Ease of Compliance Enforcement |
|
✔ |
|
Software Supported |
Windows 7 and above, 32 and 64 bits |
● Microsoft Office ● G Suite ● Box ● Salesforce |
The following are the factors that are needed to be taken into consideration when choosing between these 2 products. The key difference between these two products is that Sophos Intercept X Advanced with EDR protects internal data stored in the physical hardware whereas Druva inSync supports data stored on the cloud premises.
If you wish to find out more information on Sophos Intercept X Advanced with EDR or Durva inSync, you can visit us at Netpluz. Alternatively, you may book an appointment here for a free consultation.
Author: Jeyani D/O Ravichandran
References:
- “What Is Cybersecurity?” Cisco, Cisco, 10 Dec. 2019, https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html.
- Tay, Rachel. “Businesses in Singapore Lost Nearly S$58 Million to Email Impersonation Scams Last Year: CSA Report.” Business Insider Singapore, 19 June 2019, https://www.businessinsider.sg/businesses-in-singapore-lost-nearly-s58-million-to-cyber-attacks-last-year-csa-report/.
- Cybercrimemag. “Cybercrime Damages $6 Trillion by 2021.” Cybercrime Magazine, 9 Dec. 2018, https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/.
- Kratikal Tech Pvt Ltd. “Humans Are the Weakest Link in the Information Security Chain.” Medium, Medium, 6 Mar. 2018, https://medium.com/@kratikal/humans-are-the-weakest-links-in-cyber-security-of-any-organisation-ac04c6e6e71.
- “The Human Factor in IT Security: How Employees Are Making Businesses Vulnerable from Within: Kaspersky Official Blog.” Daily English Global Blogkasperskycom, https://www.kaspersky.com/blog/the-human-factor-in-it-security/.
- “81% Of Company Data Breaches Due to Poor Passwords.” TraceSecurity, 10 Dec. 2019, https://www.tracesecurity.com/blog/articles/81-of-company-data-breaches-due-to-poor-passwords.
- Mical, Jason, et al. “11 Ways Employees Can Be Your Weak Link for Cybersecurity.” Security Boulevard, 9 Sept. 2019, https://securityboulevard.com/2019/09/11-ways-employees-can-be-your-weak-link-for-cybersecurity/.
- SOPHOS Intercept X, SOPHOS, https://www.sophos.com/en-us/medialibrary/PDFs/factsheets/sophos-intercept-x-dsna.pdf.
- “Druva InSync Review: Pricing, Pros, Cons & Features.” com, 12 Aug. 2019, http://comparecamp.com/druva-insync-review-pricing-pros-cons-features/.
- “Synchronized Security.” Synchronized Firewall & Endpoint Protection with Sophos, https://www.sophos.com/en-us/lp/synchronized-security.aspx.
Importance of cybersecurity for cyber-attacks
Why do we have fire drills when we hardly or never encounter fire? The same goes for cybersecurity – we do not know when we will encounter a cyber-attack. Cybersecurity is the practice of protecting systems, networks and programs from digital attacks. Successful cybersecurity has multiple layers of protection spread across computers, networks, programs or data that one intends to keep safe. 1
Impact of cyber-attacks on companies
Cyber-attacks can cause financial loss for the business as well as reputational damage. When there is a loss in customers’ data to hackers, it has resulted in a fall of many companies. Companies have risk falling into endless lawless and may declare bankruptcy when customers’ data are stolen by hackers. Data recovery takes time and can be very expensive. 2 Due to reputational damage to the company, customers will lose trust in it and hence venture to other companies. Therefore resulting in a loss of profits and sales.
In March 2018, data tied to Under Armour’s fitness application was breached and affected 150 million users. Information such as user names, email addresses, passwords was stolen but users’ credit card data and social security or driver’s license numbers were not breached. During after-hours trading, Under Armour’s stock dropped more than 2%. 3
Ways employees’ actions make companies vulnerable to cyber attacks
- Outdated software
The software requires ongoing updates and upgrades. Software becomes outdated when it does not have updates to support it.4 According to PC Trends report 2019,5 1 in 6 Windows 7 users and 1 in 10 Windows 10 users are using an outdated operating system version. Outdated software does not have patches if vulnerabilities are found, resulting in more advanced cyber-attacks. Therefore, it is important to update the software as not updating it expose the business to vulnerabilities and security risks.

- Weak login credentials
Employees having weak or the same passwords across multiple accounts can allow cyber-attacks to take place easily. Principle researcher, Jarno Niemela at F-secure 5 stated that the Brute force attack is the primary way hackers use to bypass the security. It is accounted that 31% of cyber-attacks used this method to hack into their target. Brute force attack means inputting as many passwords possible, seeing if it works against their target. Hackers even have automated scripts that can find a way around simple protection, such as the maximum number of tries of passwords within a certain time window. 6 Hence a simple and common password can easily fall prey to the next cyber-attack.

- Opening unknown emails
In today’s world, emails are the most preferred way of communications when it comes to business-related context. Companies normally collect and stores a huge amount of personal data.7 In order for all of these personal data to be well taken care of, employee’s knowledge and care can play an enormous part in preventing a cyber-attack from happening. A research done by ‘The Radicati Group’8 shows that an average person needs to go through 235 emails a day. With these large amounts of emails, it is not surprising that some may contain scams in the form of attachments or links. With an accidental click, employees may be opening the gates to those cybercriminals into the company’s digital home.
Products available to reduce cyber attacks

Endpoint protection with EDR
EDR means endpoint detection and responses. Its solutions are designed to monitor and respond to advanced internet threats continuously.
- Remove malware
Endpoint protection provides simple security for business. It automatically removes malware when detected or isolates comprised devices in order to prevent damage. Below are some ways of how endpoint protection removes malware. 9
-
- Isolate devices
In order to prevent the problem from spreading further, part of rectifying a problem is to put it in quarantine. Comprised devices will be isolated when necessary until companies ensure they are safe.
-
- Threat removal
As employees may not be aware of malicious links, attachments or downloads, cyber-attacks may occur once employees click onto those. Therefore with endpoint protection, it will help to remove if anything malicious is found. It is simple and automatic.
-
- Synchronised security
Synchronised security transforms threat detection when threat discovery, investigation and response are automated. The incident response time is reduced exponentially and tactical resources can be refocused on strategic analysis.
- Decloaking malware
-
- Behavioural analytics
It helps to find out any suspicious behaviours and allow the detection of malware that is specifically designed to avoid traditional solutions.
-
- Traffic detection
It helps to pre-filter all Hypertext Transfer Protocol (HTTP) traffic and tracks suspicious traffic. Additionally, the file path of the process for the sending of malicious traffic.
-
- Integrated endpoint and network
Suspected system of what exactly firewall is detecting is alerted when there is immediate and automatic communication between Endpoint and Network. It allows the endpoint protection agent to instantly use the information to find out the process behind the attack.
Endpoint backup
Endpoint backup ensures regulatory compliance and improves data visibility for a mobile workforce. It allows employees to protect the corporate data at their convenience. It helps to protect and manage the data across all endpoints such as laptops and smartphones. The unified visibility and search across the data deliver fast identification for governance. To ensure zero-impact to the productivity of end-users, lightweight with tunable resource controls are used. 10
Summary
|
Technology |
Benefits |
|
Endpoint protection with EDR |
· Removes malware o Isolate o Threat removal o Synchronised security
· Decloaking malware o Behavioural analytics o Traffic detection o Integrated endpoint and network |
|
Endpoint backup |
· Ensures regulatory compliance · Improves data visibility · Protects cooperate data at convenience · Fast identification · Zero impact to productivity |
Conclusion
Your company can be a victim of cyber-attack just because of a small mistake made by your employees. Prevent your company from having reputational damage and facing financial losses due to cyber-attacks. Act fast before it is too late!
Click here to find out more about ways or products available to protect your data, or email us to arrange for an appointment with our experienced manager. We will provide ways for you to become more secure.
Author: Toh E Pyn
References
- Services, P. (2019). What Is Cybersecurity?. [online] Cisco. Available at: https://www.cisco.com/c/en_sg/products/security/what-is-cybersecurity.html [Accessed 11 Dec. 2019].
- com. (2019). How cyber attacks impacts business.. [online] Available at: http://www.webrtcworld.com/topics/from-the-experts/articles/440430-how-cyber-attacks-impacts-business.htm [Accessed 11 Dec. 2019].
- Anon, (2018). Under Armour announces data breach, affecting 150 million MyFitnessPal app accounts. [online] Available at: https://www.washingtonpost.com/news/the-switch/wp/2018/03/29/under-armour-announces-data-breach-affecting-150-million-myfitnesspal-app-accounts/ [Accessed 11 Dec. 2019].
- Parker Software. (2019). The security risks of outdated software – Parker Software. [online] Available at: https://www.parkersoftware.com/blog/the-security-risks-of-outdated-software/ [Accessed 11 Dec. 2019].
- Windows Report | Error-free Tech Life. (2019). 55% of Windows PCs are running outdated software [Security Alert]. [online] Available at: https://windowsreport.com/outdated-software-security-risks/ [Accessed 11 Dec. 2019].
- Palmer, D. (2019). Ransomware attacks: Weak passwords are now your biggest risk | ZDNet. [online] ZDNet. Available at: https://www.zdnet.com/article/ransomware-attacks-weak-passwords-are-now-your-biggest-risk/ [Accessed 11 Dec. 2019].
- com. (2019). Weak and Stolen Passwords | WatchGuard Technologies. [online] Available at: https://www.watchguard.com/wgrd-solutions/security-topics/weak-and-stolen-passwords [Accessed 11 Dec. 2019].
- com. (2019). [online] Available at: https://www.kaspersky.com/resource-center/preemptive-safety/7-ways-to-cyberattack-vulnerability [Accessed 11 Dec. 2019].
- com. (2019). [online] Available at: http://www.radicati.com/wp/wp-content/uploads/2015/02/Email-Statistics-Report-2015-2019-Executive-Summary.pdf [Accessed 11 Dec. 2019].
- com. (2019). Sophos Endpoint Protection. Advanced Security with Intercept X.. [online] Available at: https://www.sophos.com/en-us/products/endpoint-antivirus.aspx?cmp=36476&utm_source=GoogleSearch&utm_medium=cpc&utm_campaign=MG-ASEAN-GoogleSearch&utm_content=SM100289&gclid=Cj0KCQiA_rfvBRCPARIsANlV66MbtXXPIGuBJKxEogN28oUqQ4DVaWc9RDWV4eCoEqvCVa3-wTPZn7IaAkVnEALw_wcB [Accessed 11 Dec. 2019].
An ounce of prevention through Vulnerability Assessment and Penetration Testing (VAPT) is worth a pound of cure
We all have witnessed the notorious cyber-attacks like WannaCry and NotPetya/ExPetr.1 These high profile attacks have resulted in large disruptions, forcing businesses to halt their operations that may cost them billions of dollars.
According to Accenture, 43% of cyberattacks are targeted towards small businesses. Yet, only 14% are capable of defending against these malicious attacks.2
Obviously, a comprehensive security service will incur additional expenses. However, according to Hiscox, these cyber-attacks can cost your business on average $200,000 regardless of the scale of your business.2
Regardless of the size and scope, your business is greatly vulnerable to cyber-attacks. It is not a matter of if, but it is a matter of when you will be the next target of the hackers’ “hit list”. When it happens, your business may suffer unfathomable consequences.
Stay Free from Cyber Attacks
Now knowing your vulnerability, how can you prevent such malicious cyber activities from occurring? The most ideal and unsurpassable method is through Vulnerability Assessment and Penetration Testing (VAPT). So, you might wonder what this long piece of jargon is about and how and how it is going to protect your business.
This blog article will provide you with some valuable information on:
1. A better comprehension on VAPT
2. How VAPT is executed
3. How VAPT will improve your IT security
What is Vulnerability Assessment & Penetration Testing (VAPT)? 3
To put it in the simplest terms, Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive and extensive testing process. Its goal is to identify security flaws in your network, application or program.
As the name implies, there are two separate components to perform VAPT. Both Penetration Testing and Vulnerability Assessment execute two completely different types of security tests:
- Vulnerability Assessment: Finds flaws and vulnerability in software, network or program. In other words, to assess how defenceless your systems are.
- Penetration Testing: Conducted after identifying the Vulnerabilities. Security professionals will check and exploit the existing vulnerabilities identified in the software, network or program.
What is Vulnerability Assessment?
By pure definition, the word “Vulnerability” means being exposed to the possibility of getting attacked or harmed. Similarly, a Vulnerability Assessment will provide you with a list of possible security vulnerabilities in your company’s network.
Vulnerabilities can be the result of weak passwords, software errors, wrong software settings, computer virus, or other forms of malicious script or SQL injections.4
Vulnerability Assessment is performed using a non-intrusive approach. With the amalgamation of manual and automated scans, this will enable you to identify security flaws that may be exploited during a cyber-attack.
Here is an example to give you a better grasp on what is a vulnerability and an exploit: If an intruder could bypass the security guard at the front gate by entering the building through a backdoor – this is a vulnerability. If he/she actually get into the building – this is an exploit. It is important to understand the difference between these two words as we will be using it frequently in this blog.
What is Penetration Testing? 3
On the contrary, Penetration Testing employs an intrusive approach. Why would we say it is intrusive? Well, penetration testers would actually attempt to exploit identified vulnerabilities to gain unauthorized access into your IT infrastructure. In a way, it emulates a “real attack” to your IT network.
Upon successfully performing a penetration test, this would allow you to determine how robust your organisation is when it comes to defending your IT network.
The following information will help you understand how these tests are performed for your business.
How are Vulnerability Assessments Performed? 5
As mentioned previously, manual and automated testing tools are utilised to scan your IT infrastructure and environment for known vulnerabilities. During the assessment process, it involves three periodic steps: Assessment, Identifying Exposures and Addressing Exposures. Let’s look at each phase briefly:
1. Assessment
Assessment includes information gathering, defining the parameters and informing the appropriate personnel in your company on the procedure of the assessment.
2. Identify Exposures
This step includes reviewing the results from the previous assessment (the first step) and rectify the vulnerabilities by forming alternative actionable solutions for your network.
3. Address Exposures
At the final step, an investigation is carried out to determine if there are pregnable services in your IT infrastructure. If such vulnerabilities transpire and if the services are not critical to your business, they should be disabled.
Once these security weaknesses are reaffirmed from the investigation, your company will be informed of any lingering and unpatched vulnerabilities. These need to be rectified and patched by your company to mitigate the risk of a cyber-attack.
How are Penetration Tests Performed? 5
Now that you understand how Vulnerability Assessments are performed, the following 5 steps will briefly describe how a Penetration Test is carried out on your IT infrastructure:
1. Planning & Preparation
The very first step will involve developing clear objectives and scope of the penetration test. The details will include the time, duration and potential impact to your business operations during the penetration test.
2. Information Gathering and Analysis
At this step, a list of potential targets will be formed to be evaluated during the vulnerability assessment. These targets identified are established based on the accessible systems within your IT framework.
3. Vulnerability Detection
Similar to a Vulnerability Assessment, to identify vulnerabilities in your network, penetration testers will utilize manual and automated tools.
4. Penetration Attempt
After performing the third step (Vulnerability Detection), penetration testers would identify suitable targets to begin an intrusive attack to test the system’s defences. All these tests are performed at the within a particular time frame that you have agreed upon.
5. Reporting and Cleaning
Last but not least, a report will be summarised and submitted to you. They include: The Penetration Testing Process; Vulnerability Analysis; Commentary of Vulnerabilities Identified.
You could be worried that these exploitation attempts during tests could affect your IT systems. Do not fret.
To ensure that your accustomed business operations are not affected, the final step will require a complete mandatory clean-up of your systems during the penetration test.
We are sure on what we have shared above have overloaded you with information that could be difficult to digest. Not to worry, here is a quick summary about Vulnerability Assessment and Penetration Testing (VAPT):5
|
|
Vulnerability Assessment (VA) |
Penetration Testing (PT) |
|
Purpose: |
Identify exploitable security vulnerabilities in your IT network. |
Perform actual staged attacks and exploit all vulnerabilities in your IT network. |
|
Type of Reports Provided: |
A list of vulnerabilities that will require patches. The vulnerabilities are sequenced based on its criticality. |
A specific and detailed list of information regarding the data compromised and vulnerabilities exploited. |
|
Characteristic: |
List-oriented |
Goal-oriented |
|
Steps to Perform VA/PT: |
3 Steps:
|
5 Steps:
|
Benefits of VAPT6
We do understand if your company were to invest its money and resources in cybersecurity solutions, there need to be a substantial benefit.
If the above information did not convince completely on why you should fund and conduct such IT security tests yet, consider the following three major benefits that VAPT will bring to your business:
1. Extensive application and data security:
Your business will have the confidence that your internal and external systems, software and applications will be meticulously validated for vulnerabilities.
In addition, VAPT assists your business in constructing more secure applications, improving data security and protecting your intellectual property.
2. Improved compliance standards:
You would have heard of PCI-DSS, ISO/IEC 27002 and other security standards that your company have to oblige due to certain regulations. If you are not in compliance with them, expensive fines could be incurred to your company.
To make this process easier for you, VAPT testing identifies if your IT infrastructure is in compliance with the industry standards and government regulations.
3. Security is built into the process during development:
VAPT provides an efficient and practical method to build secure software, application or program. The primary reason for this is that security is part of the development process.
In the event that your IT network gets compromised, it will require expensive fixes and patches after a vulnerability has been exploited by an attacker. – Wasting unnecessary time, money and resources.
4. Simplify your IT network security
While reading through this blog, you must be wondering, understandably so, how you can manage such complicated cybersecurity solutions. You can see how complex it is to perform VAPT itself.
Here is another issue. If you are always being bombarded with various IT security services and needing to purchase them from different vendors, this becomes a continuous hassle and cost. At Netpluz Asia, we simplify this for you with our managed Security Operations Centre (SOC).
As the popular saying goes, “Prevention is better than cure”. Our SOC can deliver industry-leading tools, technology and expertise to secure your valuable digital assets around the clock at a fraction of the cost. If you wish to find out more about our Managed Security Services, please click here.
Summary
Currently, most enterprises are well equipped with sophisticated and highly efficient security apparatus and software. Hackers are constantly looking for new vulnerabilities to hack into your systems. As a result, cybersecurity has become the most crucial component of any company’s infrastructure.
Vulnerability Assessment is one of the first steps in improving your IT security within your business. When it is executed together with Penetration Testing the two combined operations will create a strong deterrent to cyber-attacks that target your company. Identifying security loopholes and possible damages they can pose are important factors you need to pay attention to when protecting your network from malicious attacks.
This is why many companies have been taking care of their digital assets through VAPT testing. It is an obvious fact that IT security services would incur additional costs for your company, but it is less costly than having your network system partially or fully compromised.
If you wish to find out more information on how you can protect and defend your IT business network through Vulnerability Assessment and Penetration Testing (VAPT), you can visit us at Netpluz 24/7. Alternatively, you may book an appointment by submitting your information here for a free consultation.
Author: Shaun Nisal Peiris
Reference
1 Snow, John, et al. “Top 5 Most Notorious Cyberattacks.” Daily English Global Blogkasperskycom, https://www.kaspersky.com/blog/five-most-notorious-cyberattacks/24506/.
2 Scott Steinberg, special to CNBC.com. “Cyberattacks Now Cost Companies $200,000 on Average, Putting Many out of Business.” CNBC, CNBC, 13 Nov. 2019, https://www.cnbc.com/2019/10/13/cyberattacks-cost-small-companies-200k-putting-many-out-of-business.html.
3 “Vulnerability Assessment and Penetration Testing.” Veracode, 22 Oct. 2019, https://www.veracode.com/security/vulnerability-assessment-and-penetration-testing.
4 Infosec, Cyberops. “What Is VAPT and Why Would Your Organization Need VAPT?” Medium, Medium, 15 May 2019, https://medium.com/@cyberops/what-is-vapt-and-why-would-your-organization-need-vapt-444a684c8933.
5 “Vulnerability Assessment and Penetration Testing.” Cyber Security Agency, https://www.csa.gov.sg/gosafeonline/go-safe-for-business/smes/vulnerability-assessment-and-penetration-testing.
6 Prole, Ken. “Vulnerability Assessment and Penetration Testing (VAPT).” Code Dx, 15 Feb. 2019, https://codedx.com/blog/the-perfect-union-vulnerability-assessment-and-penetration-testing-vapt/.


.png)