Webinar Recording | Fight Against the Rise of Ransomware
Click the video to play – Source:Youtube.com
Stories of organizations crippled by ransomware regularly dominate the IT news headlines, and accounts of six- and seven-figure ransom demands are commonplace. But, do the news stories tell the full story?
Based on an independent survey of 5,000 IT managers across 26 countries, the findings provide brand new insight into what actually happens once ransomware hits. Be prepared to be surprised.
Watch the webinar recording to discover:
• How many organisations were hit by ransomware last year, and which countries suffered most
• Which industries are hit hardest by ransomware (hint: it’s not the public sector)
• How many organizations pay the ransom to get their data back, and how many use backups
• The Cyber Security and Data Protection strategy
Presentation slides to view
Cyber Security is the protection of not only internet-connected systems (including hardware, software or electronic data) from theft or damage by cybercriminals but also from disruption of services following a successful cyber-attack.[1] According to the Cyber Security Agency of Singapore, 378 business email impersonation scams were recorded in 2018. This led to businesses in Singapore suffering close to S$58 million in losses. [2] Cybersecurity Ventures has reported that businesses will lose approximately $6 trillion to cyber-crime by 2021. [3]
One of the key challenges faced by organisations today is implementing cybersecurity measures to protect their internet-connected systems from the continuously evolving nature of cyber-attacks. And according to Code 42, 78% of security professionals believe that the biggest threat to cybersecurity is the negligence of employees. [4]
Cybercriminals exploit the weakest links in an organization’s IT security fabric. Often, the weakest link in any organisation is the employees. And yet a study of over 5,000 businesses around the globe by Kaspersky Lab and B2B International found that just over half of businesses (52%) believed that their cybersecurity would be at risk because of their employees. [5]

Common Cybersecurity Mistakes Made By Employees
In this section, we’ll be looking at the four principal errors made by employees that could expose organisations to cyber-attacks
1. Weak and Vulnerable Passwords
According to security experts, poor password management contributes to 81% of the data breaches.[6] With employees utilising the same password for multiple accounts, not changing passwords on a regular basis and using weak passwords (some examples as shown in the table below) put organisations at risk. [7]
Examples of weak passwords:
|
Password |
Type |
|
kathy5 |
Name-based |
|
Qwerty |
Keyboard sequence |
|
AbcAbc |
Repeating sequence |
|
dr1v3way |
Word-based with common letter and number substitution |
- Weak or Outdated Security Software
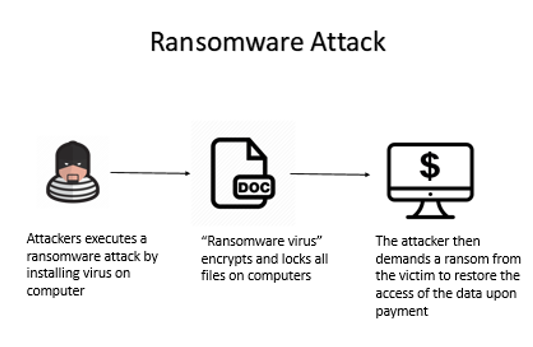
Keeping security software, web browsers and operating systems updated with the latest protection will deter cybercriminals from leveraging system vulnerabilities. However, many organizations do not keep up with the updates or fail to understand the consequences of not doing so. The consequences of an employee’s negligence could lead to a ransomware outbreak where the virus encrypts and locks all the files on the computer. The attacker then demands a ransom from the victim to restore the access of the data upon payment. [7]
Here is a diagram to illustrate how a Ransomware Attack is executed:
- Lax Email Practices
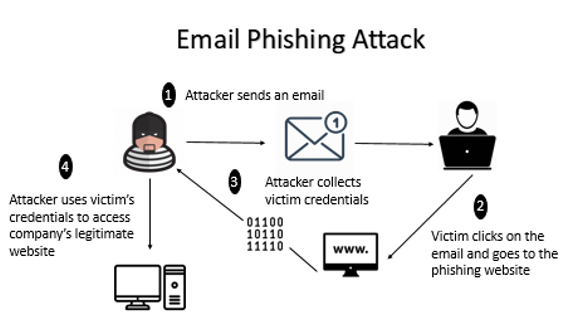
Despite repeated warnings against responding to unsolicited emails or text messages, employees continue to be targets of cyber-attacks such as phishing, social engineering, and smishing. These attacks occur when an attacker sends an email link to the victim. Upon clicking on the link, the victim will be directed to the phishing website where the attacker is able to collect the credentials of the victim. The attacker then uses the victim’s credentials to access the legitimate company’s website. [7]
Here is a diagram to illustrate how Email Phishing Attack is executed:
- Using Unsecured Networks
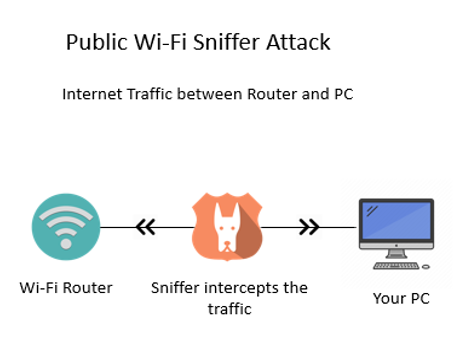
Utilising company devices on unknown networks increases the risk of cyber-attacks since data may not be encrypted over these networks and could easily be intercepted and subsequently stolen. For example, login details information can be revealed when there is an attempt to access emails on a public network. [7]
Here is a diagram to illustrate how a Public Wi-Fi Sniffer Attack is executed:
How can your company reduce these vulnerabilities?
In recent years, cyber-attacks have become more sophisticated and persistent due to weak security regulations enforced by companies. By now, you might be wondering how you could protect your data better. Sophos Intercept X Advanced with EDR and Druva inSync offer some possibilities that could help companies overcome poor practices done by their employees. These two products address the business challenges faced by organisations such as data protection, secure file sync and sharing, etc.
What is Sophos Intercept X Advanced with EDR?
Sophos Intercept X Advanced with Endpoint Detection and Response (EDR) is designed to stop the widest range of attacks. It can detect malware, provide exploit protection, defend against ransomware and more through a combination of modern and leading-edge foundation techniques. In an event of malicious activity, EDR provides users with a complete solution by providing them with a detailed report of the attack. This helps businesses understand the root cause of the attack and help them to avoid future cyber-attacks. [8]
Benefits of Implementing Sophos Intercept X Advanced with EDR

1) Deep Learning Malware Detection
Intercept X’s artificial intelligence is a deep learning neural network, an advanced form of machine learning that detects known and unknown malware without relying on signatures. Powered by deep learning detection, Intercept X has the best malware detection platform in the industry. This allows Intercept X to detect malware that slips by other endpoint security tools. [8]

2) Secured Data & Files
Intercept X utilises CryptoGuard technology to combat cyber security attack such as ransomware and boot-record attacks, making it the most sophisticated anti-ransomware technology available. Even if trustworthy files or processes are manipulated or stolen, CryptoGuard is able to interrupt and revert them to their original state. [8]
3) Detailed Report Analysis
With EDR, most threats are stopped before they can cause damage. Intercept X Advanced with EDR provides additional cybersecurity assurance with the ability to detect, investigate and respond to potential security threats. Thus, when a potentially suspicious file is detected the administrators are provided with an analysis of what the malware did and how it was executed. This helps your companies to understand the threats better and prevent them. [8]
Here is a quick overview of how Sophos Intercept X Advanced with EDR works:
What is Druva inSync?
Druva inSync provides a comprehensive solution for enterprise-grade data protection and management. It allows users to view their data sources and usage activities to ensure compliance. Administrators are also updated of any potential data risks that have been detected. Data collected are stored in a central repository, giving end-users seamless and constant access to the information. [9]
Benefits of Implementing Druva inSync
1) Centralised Data
Druva inSync allows collection of data through multiple devices like mobile phones and cloud-based applications. The collected data will be then stored and indexed in a central repository which makes it easier for an IT department to implement company policies. [9]

2) Real-Time Data Monitoring
Druva inSync is equipped with an administrative dashboard where users can monitor their data activities and data usage in real-time. This allows administrators to easily discover compliance issues and resolve them quickly before they grow into larger problems. Real-time data monitoring also keeps your organisations safe. [9]
3) Ease of Compliance Enforcement
Druva inSync helps you save time when it comes to administering policies and regulations. This system comes with pre-configured compliance templates like PCI, GLBA and HIPPA. It also enables users to customise and create their own templates. Whichever template one chooses, one can be ensured that the app automatically search for any data risks. [9]

What other solutions can you integrate along with Sophos?
Cyber-attacks are carried out mostly through emails and unsecured networks. This could be resolved by integrating the following products with Sophos Intercept X Advanced with EDR. [10]
|
Solutions: |
Features: |
|
Intercept X and Sophos Email |
✔ Validates if malware has been installed on devices with compromised mailboxes |
|
Intercept X and Sophos Wireless |
✔ Blocks worm-like lateral movement, automatically isolating infected machines ✔ Prevents non-compliant devices from connecting to corporate data |
Summary- Sophos Intercept X Advanced with EDR and Durva Insync
There are many comprehensive cyber security products available in the market to mitigate cyber-attacks. Needless to say, the product chosen to safeguard the data plays a major role in preventing cyber-attacks against your companies.
Here is a quick summary of the benefits of Sophos Intercept X Advanced with EDR and Durva InSync:
|
|
Sophos Intercept X Advanced with EDR |
Durva inSync
|
|
Deep Learning Malware Detection |
✔ |
|
|
Secured Data Files |
✔ |
|
|
Detailed Report Analysis |
✔ |
✔ |
|
Centralised Data |
|
✔ |
|
Ease of Compliance Enforcement |
|
✔ |
|
Software Supported |
Windows 7 and above, 32 and 64 bits |
● Microsoft Office ● G Suite ● Box ● Salesforce |
The following are the factors that are needed to be taken into consideration when choosing between these 2 products. The key difference between these two products is that Sophos Intercept X Advanced with EDR protects internal data stored in the physical hardware whereas Druva inSync supports data stored on the cloud premises.
If you wish to find out more information on Sophos Intercept X Advanced with EDR or Durva inSync, you can visit us at Netpluz. Alternatively, you may book an appointment here for a free consultation.
Author: Jeyani D/O Ravichandran
References:
- “What Is Cybersecurity?” Cisco, Cisco, 10 Dec. 2019, https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html.
- Tay, Rachel. “Businesses in Singapore Lost Nearly S$58 Million to Email Impersonation Scams Last Year: CSA Report.” Business Insider Singapore, 19 June 2019, https://www.businessinsider.sg/businesses-in-singapore-lost-nearly-s58-million-to-cyber-attacks-last-year-csa-report/.
- Cybercrimemag. “Cybercrime Damages $6 Trillion by 2021.” Cybercrime Magazine, 9 Dec. 2018, https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/.
- Kratikal Tech Pvt Ltd. “Humans Are the Weakest Link in the Information Security Chain.” Medium, Medium, 6 Mar. 2018, https://medium.com/@kratikal/humans-are-the-weakest-links-in-cyber-security-of-any-organisation-ac04c6e6e71.
- “The Human Factor in IT Security: How Employees Are Making Businesses Vulnerable from Within: Kaspersky Official Blog.” Daily English Global Blogkasperskycom, https://www.kaspersky.com/blog/the-human-factor-in-it-security/.
- “81% Of Company Data Breaches Due to Poor Passwords.” TraceSecurity, 10 Dec. 2019, https://www.tracesecurity.com/blog/articles/81-of-company-data-breaches-due-to-poor-passwords.
- Mical, Jason, et al. “11 Ways Employees Can Be Your Weak Link for Cybersecurity.” Security Boulevard, 9 Sept. 2019, https://securityboulevard.com/2019/09/11-ways-employees-can-be-your-weak-link-for-cybersecurity/.
- SOPHOS Intercept X, SOPHOS, https://www.sophos.com/en-us/medialibrary/PDFs/factsheets/sophos-intercept-x-dsna.pdf.
- “Druva InSync Review: Pricing, Pros, Cons & Features.” com, 12 Aug. 2019, http://comparecamp.com/druva-insync-review-pricing-pros-cons-features/.
- “Synchronized Security.” Synchronized Firewall & Endpoint Protection with Sophos, https://www.sophos.com/en-us/lp/synchronized-security.aspx.